Explained Ransomware Attack
What is Ransomware?
Any type of computer virus that encrypts and holds hostage the data of its victims is called a ransomeware. The basic information of a customer or company is encrypted, making it difficult to access documents, data sets, or apps. Then, in order to gain access, you must pay a fee. Ransomware is often meant to spread throughout an organization and target data bases and record employees, effectively shutting down the entire operation. It's a growing threat that makes hackers billions of dollars while wreaking havoc on businesses and government agencies.

How ransomware works
After a gadget is presented to the noxious code, the ransomware assault continues as follows. Ransomware can stay torpid on a gadget until the gadget is at its generally powerless, and really at that time execute an assault.
There are an assortment of conveyance channels for ransomware, however a phishing email is the most well known. Let's assume you get an email from an online retailer, expressing that you were cheated and are expected a discount. You absentmindedly click the connection, without seeing that the URL is a little off or the errors the message contains, and BAM! The ransomware assault in progress in the accompanying seven phases;
- Infection
Ransomware is secretively downloaded and introduced on the gadget. In this stage the malignant code is downloaded and code execution starts. Now your framework has been contaminated with ransomware, anyway none of your records are encoded at this point. Encryption is a reversible numerical estimation that is a fairly high CPU serious undertaking. In a common ransomware assault, It doesn't happen promptly in light of the fact that it requires some investment for the malware to decide the extent of information to encode.
It's essential to take note of that now, all your computerized identification controls have fizzled. Your firewall, intermediary, antivirus arrangement, and interruption location framework have all permitted the traffic.
- Execution
Ransomware sweeps and guides areas for focused document types, including privately put away records, and planned and unmapped organization available frameworks.
Here is when things begin to hinder a smidgen. First the malware examines your neighborhood PC to discover documents to scramble. This can require seconds to minutes. It additionally filters for information put away in the cloud, which is synchronized through organizers and shows up as nearby information. At that point it searches for record shares. This can require hours relying upon the number of offers you have on your organization. The objective is to examine what information is accessible and figure out which level of authorizations the undermined client has (e.g., list, compose, erase).
- Encryption
Ransomware plays out a vital trade with the Command and Control Server, utilizing the encryption key to scramble all records found during the Execution step. It likewise bolts admittance to the information.
When all information is stocked, encryption starts. Nearby document encryption can happen in minutes; nonetheless, network record encryption can require numerous hours. This is on the grounds that in most ransomware assaults, information on network scrape shares are duplicated down and encoded locally. At that point the encoded documents should be transferred and the first records erased. This cycle gives you some time. Let's assume you have a 25 GB record share. It will take the neighborhood PC some time to scramble that information and afterward push it back up.
- User Notification
Ransomware adds guidance documents enumerating the compensation for-unscrambling measure, at that point utilizes those records to show a payment note to the client.
- Cleanup
Ransomware normally ends and erases itself, leaving just the installment guidance documents.
- Payment
Whenever you've arrived at this stage, your information is gone, and the aggressor is requesting installment. Also, you are presently in recuperation mode.
Casualty clicks a connection in the installment guidelines, which takes the casualty to a site page with extra data on the best way to make the necessary payoff installment. Secret TOR administrations are regularly used to exemplify and jumble these correspondences to stay away from location by network traffic observing.
- Decryption
After the casualty pays the payoff, generally by means of the aggressor's Bitcoin address, the casualty may get the unscrambling key. Be that as it may, there is no assurance the decoding key will be conveyed as guaranteed.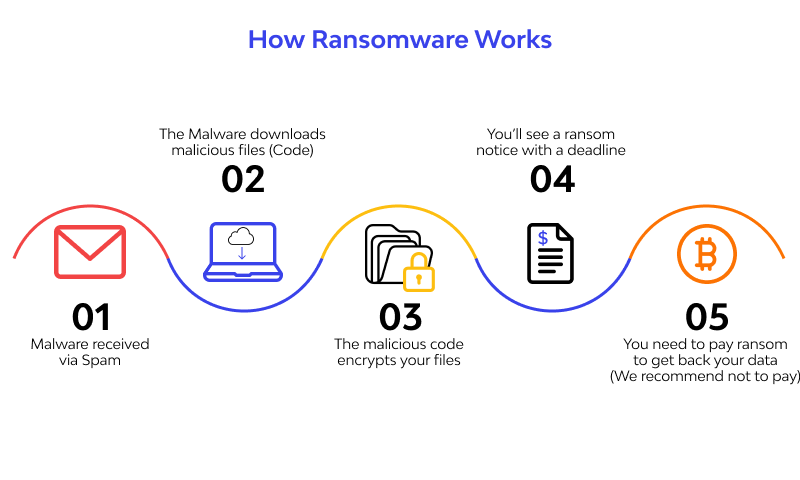
Ransomware attack protection
- Endpoint Protection
Antivirus is an undeniable initial phase in ransomware security, yet heritage antivirus apparatuses can just ensure against some ransomware variations.
Present day endpoint assurance stages give cutting edge antivirus (NGAV), which secures against sly or jumbled ransomware, fileless assaults like WannaCry, or zero-day malware whose mark isn't yet found in malware data sets. They additionally offer gadget firewalls and Endpoint Detection and Response (EDR) abilities, which help security groups recognize and block assaults happening on endpoints progressively.
- Data Backup
Assuming you reinforcement all your information, consistently, when an aggressor requests a payment of $10,000 you can relax knowing all that information they just secured or obliterated is protected on another worker that they can't contact.
In any case, you need to know how to reinforcement your information accurately. Ransomware aggressors can penetrate a reinforcement framework by going through your work area first and worming their way into your organization.
Which implies you need to reinforcement your information into the cloud – or, on a nearby stockpiling gadget that is disconnected and not straightforwardly associated with your framework. In the event that you reinforcement your information to an outside hard drive, possibly associate the hard drive when backing up your information, at that point quickly separate it.
- Application Whitelisting and Control
While boycotting is the act of forestalling the establishment of one explicit piece of programming, whitelisting is the act of permitting a particular arrangement of projects and sites – impeding the establishment or appearance of all the other things.
You first sweep a machine and distinguish all the authentic applications, at that point design it to obstruct the establishment of any extra applications.
On the web, you could introduce a promotion blocker and a content blocker to stay away from advertisements and java and blaze applications, whitelisting just the locales you consider suitable and safe.
- Patch Management
All cyberattacks and hacking endeavors attempt to misuse weaknesses inside your outsider modules and applications.
Fixing your applications assists with keeping programmers from entering your machines through openings in your introduced programming.
Java, Flash, Adobe, and so forth all should be reliably refreshed and additionally fixed to make them invulnerable.
- Email Protection
Figuring out how to forestall phishing is quite possibly the main approaches to shield yourself from a ransomware assault since most ransomware is conveyed through email.
Train representatives to perceive social designing messages, and direct penetrates to test if workers can recognize and stay away from phishing. Use spam insurance and endpoint assurance innovation to consequently hinder dubious messages, and square malignant connections if client winds up tapping on them
Likewise, malvertising, or noxious connections inserted into promotions, is another way you can get contaminated with ransomware as we've referenced before in the article. Watch out for business email bargain, don't click promotions, and stay careful.
- Network Defenses
Ransomware, as the name suggests, is a type of malware, and along these lines can be impeded on PCs by any enemy of infection or against malware motor that accurately signature-coordinates with the malevolent code. In any case, many related assaults - frequently dispatched through phishing messages, counterfeit downloads, and malevolent URLs - begin with crimeware toolboxs, which can abuse any of various weaknesses to introduce malware. Besides, when any ransomware is recognized, a tainted PC may as of now have played host to malware intended to take monetary subtleties, dispatch circulated refusal of-administration assaults or hand-off spam.
For instance, ransomware known as "Critoni," "CTB-Locker" just as "Onion," which was found in June by the malware analyst Kafeine, is being dispersed by the Andromeda bot, which initially taints PCs with an email worm considered Joleee that is intended to send spam messages and download further assault code. In late assaults, one of the records it's downloaded has been the Critoni ransomware.
Additionally, Cryptolocker was being pushed to PCs that were first tainted by Gameover Zeus. In the first place, assailants utilized Zeus to take monetary data from the PC. Afterward, they scrambled contaminated hard drives and held them to recover, subsequently expanding their benefits.
Detection and removal
Easy Ways to Detect Attack
Utilize ongoing alarming and impeding to computerize distinguishing ransomware-explicit read/compose conduct and afterward obstructing clients and endpoints from additional information access.
Use trickiness based recognition, which deliberately plants covered up documents on record stockpiling frameworks to distinguish ransomware encryption practices at the most punctual assault stage. Any compose/rename activities on the secret records naturally triggers a square of the tainted client or endpoint, while proceeding to permit access by uninfected clients and gadgets.
Utilize granular announcing and examination to give point by point review trail backing to measurable examinations concerning who, what, when, where, and how clients access records. Misdirection based recognition measure guarantees that solitary the tainted client is impeded from getting to information.
What to do after an attack?
On the off chance that you presume you've been hit with a ransomware assault, it's critical to act rapidly. Luckily, there are a few stages you can take to allow you the most ideal opportunity of limiting harm and rapidly getting back to the same old thing.
- Isolate the infected device
Ransomware that influences one gadget is a moderate burden. Ransomware that is permitted to taint the entirety of your undertaking's gadgets is a significant fiasco, and could make you bankrupt for great. The contrast between the two frequently comes down to response time. To guarantee the security of your organization, share drives and different gadgets, it's fundamental that you separate the influenced gadget from the organization, web and different gadgets as fast as could really be expected. The sooner you do as such, the more outlandish it is that different gadgets will be contaminated.
- Stop the spread
Since ransomware moves rapidly—and the gadget with ransomware isn't really Patient Zero—quick disconnection of the contaminated gadget will not ensure that the ransomware doesn't exist somewhere else on your organization. As far as possible its degree, you'll need to separate from the organization all gadgets that are acting dubiously, including those working off-premises—on the off chance that they're associated with the organization, they present a danger regardless of where they are. Closing down remote network (Wi-Fi, Bluetooth, and so on) now is likewise a smart thought.
- Assess the damages
To figure out which gadgets have been tainted, check for as of late encoded documents with bizarre record augmentation names, and search for reports of odd document names or clients experiencing difficulty opening documents. On the off chance that you find any gadgets that haven't been totally scrambled, they ought to be separated and killed to help contain the assault and forestall further harm and information misfortune. You will likely make a complete rundown of every influenced framework, including network stockpiling gadgets, distributed storage, outside hard drive stockpiling (counting USB thumb drives), PCs, cell phones, and some other potential vectors. Now, it's judicious to bolt shares. Every one of them ought to be limited if conceivable; if not, confine the most that you can. Doing so will stop any continuous encryption measures and will likewise hold extra offers back from being tainted while remediation happens. In any case, before you do that, you'll need to investigate the encoded shares. Doing so can give a helpful snippet of data: If one gadget has a lot higher number of open documents than expected, you may have recently tracked down your Patient Zero. Something else…
- Locate Patient Zero
Following the contamination turns out to be extensively simpler whenever you've recognized the source. To do as such, check for any cautions that may have come from your antivirus/antimalware, EDR, or any dynamic observing stage. Also, in light of the fact that most ransomware enters networks through pernicious email connections and connections, which require an end client activity, getting some information about their exercises (like opening dubious messages) and what they've seen can be helpful too. At last, investigating the properties of the actual records can likewise give some insight—the individual recorded as the proprietor is likely the passage point. (Remember, notwithstanding, that there can be more than one Patient Zero!)
- Identify the ransomware
You must first determine the type of ransomware you are dealing with before proceeding. One approach is to go to No More Ransom, a larger initiative in which McAfee participates. The Crypto Sheriff gadget is one of the tools available on the site to help you obtain access to your data: Simply send the software one of your encoded records, and it will search for a match. You can likewise utilize the data remembered for the payment note: If it doesn't explain the ransomware variation straightforwardly, utilizing a web index to question the email address or the actual note can help. Whenever you've recognized the ransomware and done a touch of fast examination about its conduct, you should caution all unaffected representatives at the earliest opportunity so they'll realize how to detect the signs that they've gotten tainted.
- Report the ransomware to authorities
When the ransomware is contained, you'll need to contact law requirement, for a few reasons. As a matter of first importance, ransomware is illegal—and like some other wrongdoing, it ought to be accounted for to the legitimate specialists. Besides, as per the United States Federal Bureau of Investigation, "Law implementation might have the option to utilize lawful specialists and devices that are inaccessible to most associations." Partnerships with global law requirement can be utilized to help discover the taken or encoded information and deal with the culprits. At long last, the assault may have consistence suggestions: Under the provisions of the GDPR, on the off chance that you don't inform the ICO inside 72 hours of a penetrate including EU resident information, your business could cause robust fines.
- Evaluate your backups
Presently it's an ideal opportunity to start the reaction cycle. The fastest and most effortless approach to do so is to reestablish your frameworks from a reinforcement. Preferably, you'll have a uninfected and complete reinforcement made as of sufficiently late to be advantageous. Provided that this is true, the subsequent stage is to utilize an antivirus/antimalware answer for guarantee every single tainted framework and gadgets are cleaned free of ransomware—else it will keep on locking your framework and encode your records, conceivably undermining your reinforcement.
When all hints of malware have been dispensed with, you'll have the option to reestablish your frameworks from this reinforcement and—whenever you've affirmed that all information is reestablished and all applications and cycles are back ready for action ordinarily—get back to the same old thing. Sadly, numerous associations don't understand the significance of making and keeping up reinforcements until they need them and they aren't there. Since present day ransomware is progressively modern and tough, a portion of the individuals who do make reinforcements before long discover that the ransomware has debased or encoded them, as well, delivering them totally pointless.
- Research your decryption options
On the off chance that you wind up without a reasonable reinforcement, there's as yet a possibility you can get your information back. A developing number of free unscrambling keys can be found at No More Ransom. In the event that one is accessible for the variation of ransomware you're managing (and expecting you've cleaned all hints of malware from your framework at this point), you'll have the option to utilize the decoding key to open your information. Regardless of whether you're sufficiently lucky to discover a decryptor, in any case, you're not done at this point—you can in any case expect hours or long stretches of vacation as you work on remediation.
- Move on
Regrettably, if you lack adequate troops and can't locate a decoding key, your only option may be to cut your losses and begin without any preparation. Modifying isn't a quick or inexpensive process, but if you've exhausted your other options, it's all you can do.
Example of ransomware threats
Here are the most noteworthy, fatal, and evolving ransomware threats to be aware of.
WannaCry
WannaCry is a ransomware infection that spread fast over several computer networks in May 2017. After infecting a Windows PC, it scrambles data on the hard drive, rendering them inaccessible to customers, and then seeks a bitcoin payment to decode them.
Various elements made the underlying spread of WannaCry especially significant: it struck various significant and high-profile frameworks, remembering numerous for Britain's National Health Service; it misused a Windows weakness that was suspected to have been first found by the United States National Security Agency; and it was likely connected by Symantec and other security analysts to the Lazarus Group, a cybercrime association that might be associated with the North Korean government.
The WannaCry ransomware comprises of different parts. It shows up on the contaminated PC as a dropper, an independent program that separates the other application parts implanted inside itself. Those segments include:
• An application that encodes and unscrambles information
• Files containing encryption keys
• A duplicate of Tor
The program code isn't jumbled and was moderately simple for security masters to break down. Once dispatched, WannaCry attempts to get to a hard-coded URL (the supposed off button); in the event that it can't, it continues to look for and encode records in a huge number of significant configurations, going from Microsoft Office documents to MP3s and MKVs, leaving them unavailable to the client. It at that point shows a payment notice, requesting $300 in Bitcoin to decode the records.
Cerber
Another document scrambling ransomware program called Cerber has taken unpleasantness for casualties, yet in addition reasonableness for lawbreakers, to another level. As far as usefulness Cerber isn't totally different than other ransomware dangers. It encodes records with the solid AES-256 calculation and targets many record types, including reports, pictures, sound documents, recordings, chronicles and reinforcements.
The program encodes document substance and record names and changes the first expansions to .cerber. It can likewise examine for and scramble accessible organization shares regardless of whether they are not planned to a drive letter in the PC. When the encryption cycle is done, Cerber will drop three documents on the casualty's work area named "# DECRYPT MY FILES #." They contain the payoff interest and directions on the best way to pay it. One of those records is in TXT design, one is HTML and the third contains a VBS (Visual Basic Scripting).
The VBS record is surprising. As indicated by Lawrence Abrams, overseer of the specialized help gathering BleepingComputer.com, the document contains text-to-discourse code that changes over text into a sound message.
"When the aforementioned script is performed, your PC will speak a message saying that your PC's records have been jumbled and will rehash the same thing several times," Abrams wrote in a blog article.
Locky
Another kind of ransomware, comparable in its method of assault to the infamous financial programming Dridex, is causing devastation for certain clients. Casualties are typically sent by means of email a Microsoft Word archive implying to be a receipt that requires a full scale, or a little application that does some capacity.
Macros are crippled as a matter of course by Microsoft because of the security perils. Clients who experience a full scale see an admonition if a record contains one. In the event that macros are empowered, the report will run the full scale and download Locky to a PC, composed Palo Alto Networks in a blog entry on Tuesday. A similar strategy is utilized by Dridex, a financial trojan that takes online record qualifications.
It's speculated that the gathering that conveys Locky is partnered to one of those behind Dridex "because of comparable styles of dissemination, covering record names, and a shortfall of missions from this especially forceful member agreeing with the underlying rise of Locky," Palo Alto composed.
Ransomware has demonstrated to be a gigantic issue. The malware scrambles records on a PC and now and again on a whole organization, with assailants requesting an installment to acquire the unscrambling key. Records are unrecoverable except if the influenced association has routinely supported up and that information hasn't been moved by ransomware, all things considered.
Cryptolocker
CryptoLocker ransomware is a sort of malware that encodes documents on Windows PCs, at that point requests a payoff installment in return for the decoding key. It previously arose in September 2013 in a supported assault that went on until May of the next year. CryptoLocker tricked focuses into downloading pernicious connections sent through messages. When opened, these Trojan pony connections would execute the malware covered up inside.
Not at all like infections and worms, CryptoLocker couldn't make duplicates of itself. So how did CryptoLocker spread? To assist it with contaminating extra casualties, the cybercriminals behind it utilized the now-famous Gameover ZeuS botnet. This was an organization of malware-tainted PCs that could be controlled distantly by the botnet's administrator, without the information or assent of their proprietors. As such, it was a readymade crowd for a huge CryptoLocker ransomware contamination.
In mid-2014, a global team known as Operation Tovar at last prevailing with regards to bringing down Gameover ZeuS. Thus, CryptoLocker's decoding keys were made accessible online free of charge. In spite of the fact that it's hard to nail down a precise sum, the driving forces behind CryptoLocker had effectively removed great many dollars in bitcoin from casualties by at that point. Its significant achievement has roused various other cybercriminals to create "clones" and subsidiary ransomware strains — some of which haven't yet been broken — that are either founded on the first CryptoLocker demonstrate or essentially acquire components of its name.
TeslaCrypt
At the point when recognized in February 2015, the new ransomware Trojan acquired prompt reputation as a hazard to PC gamers. Among different sorts of target records, it attempts to taint run of the mill gaming documents: game saves, client profiles, recoded replays and so on All things considered, TeslaCrypt doesn't encode records that are bigger than 268 MB. As of late, Kaspersky Lab has recognized inquisitive conduct in another danger from the TeslaCrypt ransomware encryptor family. In rendition 2.0 of the Trojan famous for contaminating PC gamers, it shows a HTML page in the internet browser which is a precise of CryptoWall 3.0, another infamous ransomware program. After a fruitful contamination, the pernicious program requests a $500 emancipate for the unscrambling key; if the casualty delays, the payment copies.
SimpleLocker
The 'SimpleLocker' Ransomware is a ransomware contamination. Ransomware like the 'SimpleLocker' Ransomware is utilized to assume control over a PC, encode the casualty's documents and specify the installment of a payment in return for admittance to the scrambled records. The 'SimpleLocker' Ransomware will change encoded documents' expansions, and drop text records containing guidelines on the most proficient method to pay the 'SimpleLocker' Ransomware emancipate. Records that have been encoded by the 'SimpleLocker' Ransomware can't be recuperated except if PC clients have the decoding key. It is the reason it is fundamental that PC clients consistently reinforcement their records, which will permit them to reestablish their encoded documents utilizing it. The installment of the 'SimpleLocker' Ransomware sum is generally completed utilizing TOR and BitCoins for secrecy.
The 'SimpleLocker' Ransomware itself isn't especially refined. These sorts of dangers are basic Trojan diseases that are appropriated utilizing ordinary danger conveyance techniques. They are not hard to carry out because of the presence of MaaS (Malware as a Service) suppliers, which permit outsiders to make their custom ransomware dangers and even deal with these dangers for them in return for an expense. The primary motivation behind the 'SimpleLocker' Ransomware is to encode the substance of the casualty's PC. To do this, the 'SimpleLocker' Ransomware checks the casualty's PC in look for pictures, recordings, archives and different documents. The 'SimpleLocker' Ransomware will encode these documents, changing their names and expansions and dropping payoff notes on the casualty's PC.
Leatherlocker
Android clients are being cautioned to be keeping watch for another sort of ransomware that takes steps to release their private information to anybody in their contact book. Named LeakerLocker, the noxious programming is being spread through counterfeit applications on the Google Play store.
Once introduced, the malware cases to have made a reinforcement of individual pictures, messages, perusing history and other delicate data. It at that point takes steps to advance these subtleties to the entirety of the client's family, companions and partners put away on the gadget, except if a payment of $50 (£38) is paid.
The ransomware was found by specialists at California-based PC security firm McAfee. The infection was found in at any rate two applications on proposal on the Play store, called Booster and Cleaner Pro and Wallpapers Blur HD. McAfee gave an admonition as of late against downloading the projects. In a blog entry, security scientists Fernando Ruiz and ZePeng Chen composed: 'We as of late found on Google Play a sort of versatile ransomware that doesn't scramble documents.
'This malware blackmails an installment to keep the assailant from spreading a casualty's private data. 'LeakerLocker professes to have made an unapproved reinforcement of a telephone's touchy data that could be spilled to a client's contacts except if it gets 'an unassuming payoff'.
Clients who do introduce the malware will see a spring up message that contains subtleties of the information it professes to have taken. It additionally holds directions of how to pay the payoff to guarantee the data is erased. It peruses: 'All close to home information from your cell phone has been transfered to our protected cloud.
'In under 72 hours this information will be shipped off each individual from your phone and email contacts list.
Wysiwye
Another sort of ransomware named WYSIWYE (What You See Is What You Encrypt) has been distinguished by analysts at PandaLabs.
As clarified in a post on the association's site, the standard ransomware method digital criminals utilize is to access a PC and afterward infer execute the comparing malware naturally to begin encryption and at last presentation the payoff message.
Be that as it may, in an examination of a new interruption, PandaLabs found a more customized kind of malware generator which permits assailants "the opportunity to modify the malware utilizing an easy to understand interface preceding dispatching it. Making it much simpler for those with minimal specialized information to target organizations."
With this modified assault, PandaLabs adds, it's feasible to hand-pick the organization PCs whose data the aggressor might want to encode, pick records, self-erase after finishing the encryption, enter secrecy mode, and so on
"Typically ransomware has its own design, it just must be executed and it will work similarly all over the place," Luis Corrons, PandaLabs specialized chief, Panda Security, told Infosecurity. "This one is intended for more custom assaults, basically in corporate organizations. In all cases we have considered (discussing this specific assault) assailants are accessing the diverse corporate organizations after a savage power assault against the far off work area association. At that point they physically drop the ransomware, run it and can design it in various manners relying upon every casualty, cautiously picking what they need to encode."
NotPetya and Petya
Petya is ransomware that taints a machine and scrambles a whole hard drive, by getting to the Master File Table (MFT). This makes the whole plate unavailable, albeit the real records are not encoded. Petya was first seen in 2016, and was spread predominantly through a phony employment form message connecting to a contaminated record put away in Dropbox. It just influenced Windows PCs.
Petya requires the client to consent to allow it to make administrator level changes. After the client concurs, it reboots the PC, shows a phony framework crash screen, while it begins encoding the circle in the background. It at that point shows the payment notice.
The first Petya infection was not exceptionally effective, however another variation, named NotPetya by Kaspersky Labs, end up being more risky. NotPetya is furnished with an engendering instrument, and can spread without human mediation.
NotPetya initially spread utilizing an indirect access in bookkeeping programming utilized generally in the Ukraine, and later utilized EternalBlue and EternalRomance, weaknesses in the Windows SMB convention. NotPetya encodes the MFT as well as different records on the hard drive. While scrambling the information, it harms it so that it can't be recuperated. Clients who pay the payoff can't really get their information back.
Ryuk
Ryuk is a modern ransomware danger that has been focusing on organizations, clinics, government foundations and different associations since 2018. The gathering behind the malware is known for utilizing manual hacking strategies and open-source instruments to move horizontally through private organizations and gain managerial admittance to however many frameworks as would be prudent prior to starting the document encryption.
Ryuk is solely appropriated through TrickBot or follows a disease with the Trojan. Nonetheless, not all TrickBot diseases lead to Ryuk. At the point when they do, the organization of Ryuk happens a long time after TrickBot first appears on an organization. This is likely in light of the fact that aggressors utilize the information gathered by TrickBot to distinguish conceivably significant organizations for Ryuk.
The objective determination is trailed by manual hacking exercises that include network observation and parallel development determined to bargain space regulators and accessing whatever number frameworks as could be allowed. This guarantees that when Ryuk is sent, the harm is quick and inescapable across the organization, which is bound to constrain an association's hand than holding only a couple of its endpoints prisoner.
GrandCrab
First saw in January of 2018, GandCrab ransomware is a kind of malware that scrambles casualties' documents and requests recover installment to recapture admittance to their information. GandCrab targets customers and organizations with PCs running Microsoft Windows.
Seeming like a physically sent sickness, one may think a name like "GandCrab" has something to do with the ransomware's irresistible nature and inclination for spreading across business organizations. As per ZDNet, nonetheless, GandCrab's name might be gotten from one of its makers who passes by the online handle "Crab" or "Gandcrab."
GandCrab doesn't taint machines in Russia or the previous Soviet Union—a solid pointer that the creator or creators are situated around there. Little else is thought about the GandCrab group. GandCrab follows an offshoot advertising plan of action, also known as Ransomware-as-a-Service (RaaS), in which low-level cybercriminals do the hard work of discovering new casualties while the danger creators are allowed to dabble with and improve their creation..jpeg)
Authentic organizations utilize offshoot models constantly, most prominently Amazon. For instance, suppose you have a blog where you survey hardware—think earphones, cell phones, PCs, PCs, and so on Each audit incorporates a novel connection that permits guests to purchase the included thing on Amazon. In return for sending the client to Amazon you get a level of the price tag.
Upon disease, emancipate notes are put noticeably on the casualty's PC, guiding them to a site on the Dark Web (the secret piece of the web you need an extraordinary program to see). Arriving on the English language form of the site, casualties are shown the grammatical mistake baffled message "WELCOME! WE ARE REGRET, BUT ALL YOUR FILES WAS INFECTED!"
Thanos
This ransomware encodes documents, alters their filenames and produces a payoff note. It renames documents by attaching the ".bolted" expansion. It implies that after encryption a document named "1.jpg" is renamed to "1.jpg.locked", "2.jpg" to "2.jpg.locked, etc. It makes the "HOW_TO_DECYPHER_FILES.txt" text record (emancipate note) in all organizers that contain encoded documents.
As written in the payment note, all documents are encoded and shadow duplicates are erased. Additionally, all records that are put away on the contaminated PC were downloaded and will be spilled if casualties won't pay emancipate. Directions on the most proficient method to pay a payment (buy an unscrambling instrument and additionally apparatuses) can be gotten by composing an email to 001002003@secmail.pro. Tragically, casualties of Thanos ransomware assault can't unscramble records without an instrument (or apparatuses) that can be given simply by its designers. As such, there are no outsider devices that can unscramble records that are encoded by Thanos, at any rate not right now.
In cases like this one the best way to recuperate petitions free of charge is to reestablish them from a reinforcement. It is beneficial to make reference to that digital hoodlums ought to no be trusted (paid), usually they don't send a decoding programming and additionally key regardless of whether casualties pay them. One more significant thing to know is that introduced ransomware can be kept from bringing on additional encryptions (on the off chance that it has not scrambled all records) by uninstalling it. In any case, documents that are as of now scrambled remain encoded regardless of whether it is not, at this point introduced.
FAQ
References
Subscribe for the latest news

















