NIST Cybersecurity Framework (CSF) 🔒 - Full Guide
Cybersecurity and privacy are crucial anxieties for all organizations due to the increasing frequency and sophistication of cyberattacks, particularly ransomware attacks. The cost of such attacks on businesses has risen significantly in recent years, and every company should have a plan for protection against them. The National Institute of Standards and Technology's Cybersecurity Framework delivers a set of fundamental program meanings that can guide an organization to greater security, and compliance with it is voluntary but highly recommended. It is widely employed in the U.S., but implementing it can be challenging.

What is the NIST Cybersecurity Framework (CSF) 2.0?
In the current landscape of hyper-connected ecosystems, the NIST Cybersecurity Framework (CSF) 2.0 serves as the definitive blueprint for digital resilience. Released as a major evolution in early 2024, version 2.0 has moved beyond its origins in critical infrastructure to become a universal language for risk management. Whether you are a small startup or a global enterprise, this framework provides the agility needed to outpace modern adversarial tactics.
Understanding the NIST Cybersecurity Framework (CSF) and Its Importance
The NIST Cybersecurity Framework (CSF) is not just a static list of "to-dos"; it is a living methodology for navigating digital uncertainty. By providing a structured taxonomy, it allows organizations to align their security investments with actual business risks.
In 2026, its importance is magnified by the rise of AI-driven attacks. With the global average cost of a data breach now climbing toward $5.1 million (Source: IBM / Ponemon Institute 2026), the CSF acts as a critical shield. It transforms cybersecurity from a "black box" technical issue into a transparent, manageable business process that can be discussed in the boardroom.
What is the NIST CSF Full Form in Security?
If you are asking about the CSF full form in security, it stands for the Cybersecurity Framework. While many frameworks exist, "The Framework" (as it’s often called) specifically refers to the standard developed by the National Institute of Standards and Technology. It has become the most widely adopted security structure in the United States, with a growing footprint across Europe and Asia, serving as the foundational DNA for modern security operations centers (SOCs).
History and Evolution: From NIST CSF 1.1 to 2.0
The transition from version 1.1 to 2.0 was a pivotal moment in cybersecurity history.
- The 1.1 Era: Focused primarily on "protecting the perimeter" of critical sectors like power grids and financial systems.
- The 2.0 Revolution: NIST acknowledged that every business is now "critical." The updated version introduced the Govern function, emphasizing that security starts with culture and policy, not just firewalls. It also placed a massive focus on Supply Chain Risk Management (C-SCRM), recognizing that your security is only as strong as your weakest vendor.
The Core Functions of the NIST Cybersecurity Framework
The framework is organized into six "Functions," which provide a high-level view of the lifecycle of an organization's management of cybersecurity risk.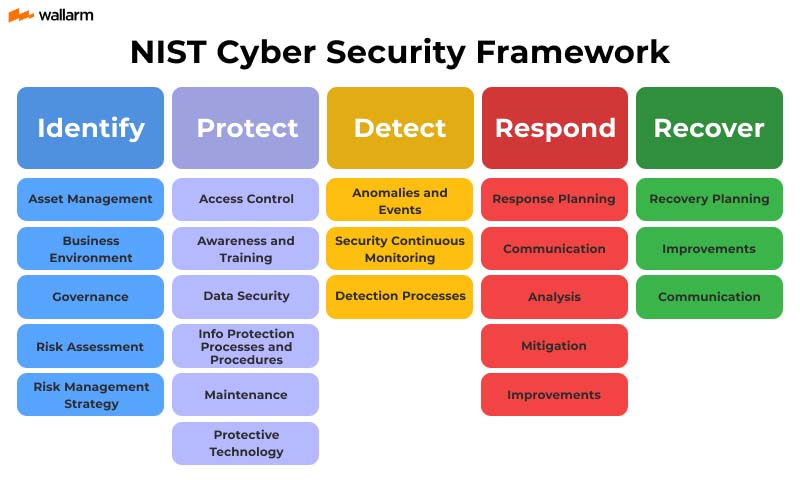
1. Govern (GV) – The New Pillar of NIST CSF 2.0
This is the "brain" of the nist cybersecurity framework. It focuses on how an organization makes decisions to support its security strategy. It covers risk appetite, roles and responsibilities, and supply chain risk management. By 2026, governance has become the top priority for 64% of organizations facing geopolitically motivated attacks (Source: WEF Global Cybersecurity Outlook 2026).
2. Identify (ID)
The Identify procedure is devoted to establishing norms and procedures for a secure and protected network. Antivirus risk management for systems, people, assets, data, and competencies can be better understood with the help of this function. This role highlighted the significance of knowing the business environment, the resources that support important functions, and the accompanying system activities to enable an entity to focus and prioritize its activities according to its risk administration strategy and business needs. Important tasks in this category include:
- Gathering information on hardware and software assets is the first step in developing an asset management strategy.
- Learning about the company's supply chain and other relevant external factors is essential.
- Determining the vulnerability management rules that will be used to design the governance program, as well as determining the legal and regulatory requirements related to the enterprise security competencies.
- Risk assessment involves the identification of asset exposures, risks to interior and exterior organizational resources, and risk response actions.
- Developing a risk administration strategy involves figuring out how much you're willing to take.
- Inaugurating a framework for making difficult decisions in the context of supervising supply chain threats, including determining preferences, limitations, danger forbearances, and underlying presumptions.
3. Protect (PR)
The Protect feature facilitates the capability to restrict the repercussions of a possible specific happening by outlining necessary prerequisites to assure the submission of vital wireframe services. In this category, the following are essential tasks:
- Safety for both on-premises and remote identity administration and permit are implemented.
- Comprehensive safety apprenticeship, including role-based and honoured user training, to equip employees.
- Data security, availability, and privacy can be ensured by instituting safeguards that are in line with the business's danger surveillance strategy.
- Maintaining and managing assurance of the safety of data and hardware requires the establishment of protocols and procedures.
- Supervision, including remote cautiousness, protects a company's resources.
- The administration of technology for the purpose of maintaining stable operation in accordance with established company policy and other applicable legal and contractual obligations.
4. Detect (DE)
This purpose establishes the right actions to take in order to detect the existence of a IT protection event in a timely fashion, which is of paramount importance. Function-related actions consist of:
- Making certain that out-of-the-ordinary occurrences are seen and the consequences of those occurrences are comprehended.
- Anti-malware possibility controls for secure operations efficacy verification via system and keeping tabs on one's fitness level with the use of constantly recording sensors.
5. Respond (RS)
This feature aids in reducing the impact of a possible cyber attack by focusing on the right things to do in that situation. Some of the essential things to do in this role are:
- Implementing pre-planned responses during and after an emergency.
- handling post-event dialoguing with interested parties both inside and outside the organisation.
- Assistance with recuperation efforts and conducting forensic investigations to better understand the scope of an issue and how best to react to it.
- Proceed with caution to limit the impact of a problem and bring about a positive resolution.
- Improving processes by leveraging knowledge gained from monitoring and responding efforts.
6. Recover (RC)
Whatever you can do or provide that were disrupted as a result of a data breaches can be restored thanks to the work done by the Recover function. In order to lessen the damage of cybercrime, it is crucial that normal operations be resumed as soon as possible. Some of the crucial steps for this function overlap with Reply, such as:
- Recovery planning entails putting into action various strategies and procedures in order to restore assets and/or systems that have been corrupted by ransomware. This can be done in order to recover from a ransomware attack.
- Putting into action enhancements discovered through examinations of current methods.
- During and after a given interaction, internal and external communications are coordinated.
NIST Framework Implementation Tiers: Measuring Maturity
The Framework Implementation Tiers describe an organization's degree of cybersecurity risk management practices, ranging from Partial (Tier 1) to Adaptive (Tier 4). Tiers consider various risk management aspects, including privacy and civil liberties, and help organizations determine their desired level of cybersecurity risk management. Tiers do not represent maturity levels, but rather support decision-making and resource allocation. Successful implementation is based on achieving Target Profile outcomes, but Tier selection affects Framework Profiles and prioritization. Tier recommendation by Business/Process Level managers influences progress assessments and sets the overall tone for cybersecurity risk management. Following are the NIST cybersecurity framework steps.
Step 1 – Partial
There is a lack of institutionalized cyber defense risk management procedures, and the organization's risk objectives, threat environment, and business/mission needs are not used to inform the prioritization of digital security actions. Vulnerability management risk management is rarely standardized and usually managed on a case-by-case basis, and there is little understanding of the risks involved at the organizational level. There is a lack of communication and cooperation within the company, therefore cyber supply chain hazards are largely unknown.
Step 2 - Risk
Management has sanctioned certain risk management procedures, but they have not been codified as official policy. Goals for risk, the nature of the threats, and business needs all factor into the prioritization of safety efforts. At the corporate level, the digital security risk is recognized, but there is no clear, company-wide strategy. Throughout the company, network security data is casually shared. The company is aware of its place in the ecosystem, but not its reliance on other entities. Sometimes, but not always, other entities are involved in the process of collaboration and information exchange. Cyber supply chain concerns are recognized within the company, but only occasionally addressed.
Step 3 - Repeatable
The organizational policy is in place for managing risks and is reviewed and revised on a regular basis to account for new risks and requirements. An enterprise-wide strategy exists for handling data breaches, along with tried-and-true procedures for dealing with emerging threats and trained staff. Top-level management keeps protection in mind across the board by encouraging open lines of communication between those responsible for IT security and those in charge of other departments. Cyber supply chain hazards are recognized, and the company has procedures in place to deal with them through collaboration and information sharing.
Step 4 – Adaptive
The company's protocols for handling issues adapts hazard mitigation strategy to new threats by using sophisticated technology and techniques. An integrated risk management program addresses attack surface and corporate objectives with risk-informed policies and procedures. Top executives assess operational risks alongside other risks, and the budget is based on present and expected risks. Administration of dangers to infosec is part of the culture and may swiftly adapt to business objectives. The company recognizes its role in the ecosystem, communicates information with collaborators, and uses real-time information to address threat of cyberattacks on distribution networks. It aggressively interacts with and maintains supply chain relationships.
Key Benefits of Adopting the NIST CSF
Why do industry leaders prioritize the cybersecurity framework?
- Risk-Based Prioritization: Instead of trying to fix everything at once, the CSF helps you identify which 20% of controls will mitigate 80% of your risk.
- Regulatory Preparedness: By aligning with NIST, you automatically meet many of the requirements for GDPR, CCPA, and various state-level privacy laws.
- Enhanced Communication: It provides a "Rosetta Stone" for security, enabling IT teams and CEOs to speak the same language regarding threat posture and budget needs.
Is the NIST CSF a Compliance Mandate or Voluntary?
Technically, for the private sector, the nist csf remains a voluntary set of guidelines. However, the market is turning it into a "soft mandate." By 2026, cyber insurance providers frequently require NIST CSF alignment as a prerequisite for coverage. Furthermore, many government contracts and B2B partnerships now include "NIST compliance" in their Master Service Agreements (MSAs). While it isn't a law, operating without it is increasingly seen as a sign of "security negligence."
How to Establish a NIST CSF Cybersecurity Risk Management Program
Building a program around the nist csf follows a circular, iterative path:
- Scoping: Define which business units or assets are most vital.
- Profiling: Create a "Current Profile" (where you are) and a "Target Profile" (where you need to be).
- Gap Analysis: This is the "Aha!" moment where you identify exactly where your defenses are failing.
- Implementation: Execute a prioritized roadmap to close those gaps.
- Continuous Monitoring: Since the threat landscape changes weekly, your NIST profile should be audited and adjusted at least once a quarter.
How the NIST CSF Integrates with Other Frameworks (ISO, SOC2)
One of the framework's best features is that it doesn't force you to "pick a side."
- ISO 27001: While ISO is a formal certification, NIST CSF 2.0 maps perfectly to its controls. Many companies use NIST for day-to-day management and ISO for the "badge" on their website.
- SOC2: The "Trust Services Criteria" of SOC2 overlap significantly with the Protect and Detect functions of NIST.
- CIS Controls: NIST provides the "Why" and "What," while CIS Controls often provide the technical "How."
FAQ
References
Subscribe for the latest news
















