Book Your API Security Demo Now
Talk to an Expert
Gain confidence in your AI adoption with security that scales.
Trusted By



One Platform.
Four Ways to Manage AI Risk.
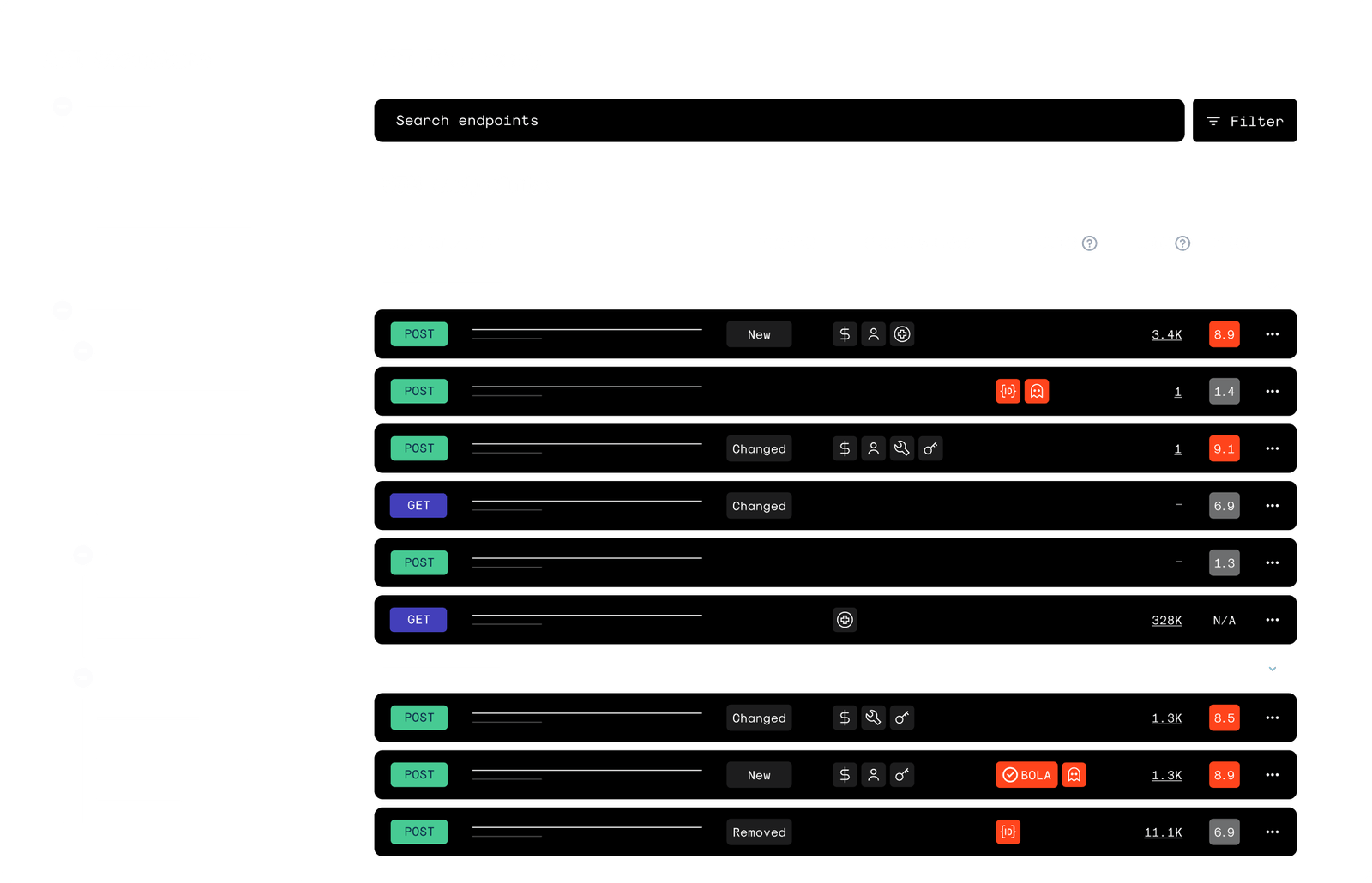
See Everything That's Exposed
APIs across environments
AI inference and model-serving endpoints
Autonomous agents and workflows
Shadow and legacy exposure

Stop Attacks Where Risk Is Real
API abuse and exploitation
Business logic attacks
Authorization failures
Token and integration misuse
AI-driven automation attacks
Find Weaknesses Before Attackers Do
Authorization boundaries
Business logic flows
Workflow manipulation
AI orchestration and integration paths


Maintain Control as AI Scales
Govern API and AI exposure
Enforce consistent security policies
Monitor risk trends over time
Provide executive and board-level visibility
It’s not API Security if it doesn’t block attacks
Wallarm is the only solution that aligns its technology and teams to stop attackers. Wallarm is easily deployed inline to block attacks and our expert API SOC team gives you peace of mind 24/7/365.
Real time
API
SOC-as-a-service
Wallarm is the Leader in API Security
Don't just take it from us. Read what security leaders and practitioners think about our platform.
read reviewsTrusted by Security.
Attackers don’t care that you watch them, they only care if you stop them. That’s why Wallarm is the preferred choice for Security teams seeking unparalleled protection and prevention capabilities.
#1
In customer reviews
160K+
APIs protected
Billions
APIs requests protected, daily
I would absolutely recommend Wallarm, in a heartbeat. They do what they say on the tin – meaning what they say they can do, they really do.











