API Security Tutorial
API security is paramount in today's digital enterprise landscape. With the rise of cloud computing, microservices, and mobile technologies, there's a heightened reliance on APIs. This demands robust security measures, including proper authentication, rate limiting, meticulous input validation, and the deployment of API gateways and API security products. Continuous API discovery, regular security testing, and proactive threat prevention are essential to safeguarding APIs against contemporary vulnerabilities. Let's unpack all of this in the article.

What is API Security?
API security is a diverse area with multiple layers. The focus of each layer is on specific API security and is designed to earn a specific and strong protection level.
API Discovery
Can you answer a simple question: "How many APIs do you have?" Identifying the APIs and managing the API inventory is a vital task for organizations that work with multiple APIs.
In a large organization, it's impractical for anyone to keep track of every API and the data each one exposes. No surprises there is a problem of shadow APIs (similar to shadow IT), API endpoints that exist within an organization's environment but are not known to, or managed by, the organization's IT or security teams.
The challenge of maintaining an API inventory intensifies when considering projections that by 2025, fewer tan half of the APIs will be actively managed. This implies a significant presence of "zombie APIs" – APIs that, while deprecated, remain accessible due to legacy systems. These unmanaged APIs are potential vulnerabilities, leaving them exposed to potential threats.
Finally, APIs go through their lifecycle. An API evolves, new versions of an API come up or an API may even be deprecated but continue to operate for a temporary period for backward compatibility and then be forgotten or gradually fall off the radar because they receive very little traffic.
API discovery is a race between API providers and hackers; the latter can easily exploit APIs once they're found. To identify your APIs before attackers do, you can analyze your API traffic from different sources. This data is sourced from API gateways, load balancers, linux kernel (eBPF) or directly from network traffic. It's then processed by a specialized engine that produces a comprehensive list of APIs. This list can subsequently be compared with the catalogs of APIs available through an API management layer.
API Real-Time Protection
Most commons API threats are well described in OWASP API Security Top-10 (see the detailed section below). You need to have proper visibility and security controls to mitigate all of these threats.
API Security Testing
As the number of APIs continues to grow, many teams are struggling with how to innovate while also ensuring security and compliance. While the shift-left concept has been around for years, it remains a challenge even for the modern orgs to successfully integrate API security testing into their engineering process.
When deploying application security tooling in your CI/CD pipeline, you need to make sure that the products and tools are adequate for your protocols. For example, if your API is mainly REST and GraphQL, make sure your SAST, DAST, IAST tooling supports those.
API Security Checklist
Watch our video in which SANS Institute Fellow Frank Kim and Wallarm co-founder Stepan Ilyin as they walk through the API Security checklist that outlines the most common API security issues, their implications, and mitigation strategies:
API Security Checklist from video guide
It can serve as a starting point for Engineering and Security teams looking to keep APIs compliant and secure.
In this checklist we have collected all the common API safety vulnerabilities and their consequences.
We also gave recommendations on how to fix them and mitigation strategies.
Why is API Security Important?
As software broke into smaller pieces and got recruited into more roles, APIs became essential, connecting the constituent parts to create a powerful sum that companies could customize to their strategy. As such, the number of APIs has exploded. To put that into perspective, there were less than 200 million APIs in 2018, but estimates suggest the total could exceed 1.7 billion by 2030.
Attackers noticed that upward trajectory and the ever-growing valuable data traveling through these vulnerable pipelines. They took aim at what was then an easy yet high-value target, beginning an onslaught of attacks that rose with the number of APIs overall. In 2022 alone, continuing a long-running trend, the number of API attacks rose by 197% according to one study, and API-related vulnerabilities grew by 78%2. In one instance, an API vulnerability at Uber led to a data breach affecting 57 million people and costing the company $148 million. APIs started to look like a high-risk asset at the same time they were proliferating faster than anyone could keep up with.
API Security vs App Security
Security teams are stretched thin despite requiring more resources than ever. Companies are paying for expensive API security solutions yet applying endless amounts of duct tape and super glue to make them work while finding workarounds for everywhere they can’t work. And despite all this effort, the frequency, severity, and damage of API attacks keeps getting worse. Little wonder, then, that there’s been a strong push to reunite application security and API security under one umbrella.
On one front, that push is coming from legacy WAF vendors. Big names in this space have recently acquired API security vendors and begun to talk about WAF and API as two sides of the same application security coin. There has not been the same effort from the startups in the API security space to add WAFs to the product line — perhaps because they have a vested interest in maintaining a separate dichotomy.
On another front, Gartner put its weight behind the concept of integrating WAF and API security. It used to have a Magic Quadrant dedicated to WAF vendors (it never had one dedicated to API security vendors), but several years ago it updated that quadrant to encompass Web Application and API Protection (WAAP). Few know the tech landscape as well as Gartner, so for them to draw an explicit link between web application and API security speaks loudly about how these tools function together and where the vendor landscape is headed — integrated not independent.
API Security Standards - Top-15 Best Practices
We talked to many product security experts about where they think everyone should begin their API security program. Here is what they said.
- Inventory all APIs
Security and engineering leaders should easily answer key questions: How many APIs are in use and where is sensitive data transferred? In 99% they can’t. It's crucial to have an up-to-date inventory of API methods and which of them handle PII and PHI data. While specialized products exist, open-source solutions like APIClarity can also aid in API discovery.
- Discovery deprecated (Zombie) and undocumented (Shadow) APIs
Zombie, Shadow, and Orphan APIs pose an enormous risk (see 2023 State of the API Report). Proper API Governance includes the process for producing and managing specifications in Dev, as well as identifying noncompliance with specs. OSS tool APIClary can help here, too.
- Deploy API gateways
Utilize API gateways for managing, monitoring, and securing API traffic (note: a lot of APIs are actually unmanaged!). This adds an essential API security layer with capabilities like Rate Limiting, Caching, Authentication, Access Control, and CORS. A lot of powerful gateways are open-sourced and have premium options including Kong API Gateway and Tyk.
- Automate API security testing
It’s always better to discover dangerous security misconfiguration and other issues in dev environment vs in production. While not exhaustive, open-source tools like ZAP, openapi-fuzzer, and RESTler provide significant value. There is not best recipe but most companies have a combination of DAST, SAST, and IAST and devtools to help developers develop secure code (such as plugins for IDEs)
- Proactively look for API Leaks
API secrets leakage can lead to serious incidents. Regularly scan for exposed credentials, including API keys, in GitHub repositories, Postman collections, and similar platforms to prevent unauthorized access. Code repositories are often spots where engineers accidentally leak API keys. Find leaked credentials with tools like TruffleHog.
- Risk score APIs to prioritize security efforts
Don’t be overwhelmed by the number of APIs to secure. Once APIs are identified, you can prioritized testing and audit based on risk factors suitable for your specific case. Consider aspects like data sensitivity (endpoints handling PII data such as names or SSN), exposure level (external vs. internal API), and the number of parameters.
- Audit existing tools to make sure they support APIs
Many security tools you trusted for years, including scanners and WAFs, may not fully protect your app estate emerging API threats. Moreover, often they don't provide protection for your API stack at all - for example, they may not analyze traffic in GraphQL or gRPC. Test your tools' protocol support using projects like GoTestWAF or use our online service - API Security testing platform.
- Comply with the OWASP Top-10 API Security Recommendations
The best place to get familiar with API threats is the OWASP API Security Top-10, or the summary we prepared for you (see the relevant section here). This list is a must-read for both security and eng teams and provides an extensive examination of significant API vulnerabilities and mitigation techniques.
- Extend Beyond OWASP
Wallarm publishes quarterly and annual API ThreatStats reports covering emerging API threats, drawing from an analysis of all known CVEs and billions of observed attacks. Consider this a dynamic and up-to-date complement to the OWASP API Security Top-10
- Use only industry-standard methods for authentication and authorization
Do not reinvent AuthN/AuthZ methods. Rely only on OAuth 2.0, JWT, OpenID Connect, and Bearer Tokens, or other industry standards for your authentication. Couple with stringent authorization checks at each API endpoint for access control. Even minor oversights in authorization have led to catastrophic data breaches in APIs over the past few years.
- Find APIs which can be abused and get ready
APIs are developed to be consumed by software and hence inherently prone to abuse. Figure out which APIs are likely to be abused and prepare a plan of action. Rate limiting and throttling are effective but not sufficient against advanced abuses. For such cases, building protection at the application level or employing specialized products is necessary.
- Use encryption for external and internal microservices
In a zero-trust environment, using mTLS between microservices is a best practice.
- Actively enforce API policies on traffic
Thoroughly validate and sanitize all user inputs to avert typical vulnerabilities such as SQL injection, SSRF, and other forms of injection attacks. A proven strategy is to validate all API calls against their specs to screen out potentially harmful requests. An effective tool for this is the open-source API firewall, which functions as a reverse proxy, validating API requests and responses based on OpenAPI and GraphQL schemas.
- Implement API logging
Maintain API logs and implement real-time monitoring to detect and respond to abnormal actions (including on the session level). This can all help to isolate ongoing incidents swiftly.
- Pay Attention to LowCode & NoCode Tools
Be aware of the implications of LowCode and NoCode tools, especially those with direct data access, as their security aspects are often overlooked. Most of them are using APIs for integrations.
API Security Leaks
API Leaks refer to the accidental or intentional exposure of sensitive data through Application Programming Interfaces (APIs). If not secured properly, APIs can expose sensitive information, such as personal data, financial information, or other types of confidential data, to unintended parties. API leaks can occur due to misconfigured API settings, vulnerabilities in the code of the API, or inadequate security protocols. These leaks can lead to severe consequences, including data breaches, identity theft, and financial loss.
There are several types of API leaks, including:
- Data leaks: These are the most common type of API leaks, where sensitive data such as personal information, passwords, and financial data are made accessible through APIs.
- Access leaks: In this type of leak, unauthorized users are granted access to restricted APIs, giving them access to sensitive data that they should not have access to
- Integration leaks: This type of leak can occur when APIs are integrated with other applications without proper security measures in place
- Supply chain leaks: These leaks occur when third-party APIs with vulnerabilities are included in the supply chain, giving attackers a means to exploit the weak points in the API
- Configuration leaks: This type of leak happens due to misconfigured APIs, where settings are not set to the desired level of security, making data vulnerable to attacks.
API Security OWASP TOP 10 Vulnerabilities

- API1:2023 (Broken Object Level Authorization): To address BOLA, detect vulnerabilities in both development and production, and consider using an inline API security tool to block attacks, especially when immediate code fixes are challenging. Risk Rating: 6.0
- API2:2023 (Broken Authentication): Start with detective controls to catch and block attacks, assess API vulnerabilities, prioritize high-risk ones, and work on fixes. If you don't control the app, collaborate with vendors with evidence and priorities. Risk Rating: 8.0
- API3:2023 (Broken Object Property Level Authorization): Identify vulnerable API endpoints, instruct developers to fix issues, and report third-party vulnerabilities. An inline API security tool can provide protection when quick fixes aren't feasible. Risk Rating: 5.3
- API4:2023 (Unrestricted Resource Consumption): Create a threat model for resource consumption, set external limits, and make risk mitigation decisions even without direct control over application code. Risk Rating: 8.0
- API5:2023 (Broken Function Level Authorization): Restrict function access in the code, maintain good API hygiene, and consider monitoring and blocking tools for better mitigation. Risk Rating: 8.0
- API6:2023 (Unrestricted Access to Sensitive Business Flows): Understand your business flows, use automated tools sparingly, employ blunt-force approaches, and maintain good API governance. Risk Rating: 5.3
- API7:2023 (Server Side Request Forgery): Ideally, restrict at the resource-fetching mechanism. If not, apply controls at the network or application layer, or use a dedicated tool to block SSRF attacks. Risk Rating: 5.3
- API8:2023 (Security Misconfiguration): Implement good security governance, create API specifications, and prioritize where to apply resources to eliminate misconfigurations. Risk Rating: 9.0
- API9:2023 (Improper Inventory Management): Begin with API discovery for better documentation, build API specifications into your development process, and request them from vendors to manage inventory properly. Risk Rating: 5.3
- API10:2023 (Unsafe Consumption of APIs): For APIs you control, implement best practices and evaluate against a checklist. For third-party APIs, validate their compliance with your checklist and establish a response plan for non-compliance. Risk Rating: 7.0
- Injection (formerly API8:2019): Injection attacks remain the most dangerous threat for APIs. Be especially aware of their risk and take proactive measures to prevent them. Risk Rating: 9.0
API Authentication Methods
The task of verifying users’ identity is imperative as it keeps ill-usage of API at bay and verifies user authenticity before granting him the access to the stored information kept for better Web API Security. It involves verifying the identity of someone who tries to view or edit the API resources, allowing only authenticated users for the same.
1. Host-based authentication
The host-based authentication schema is widely used for IOT devices and raw network authentication. It is not recommended for web technologies since it can be bypassed with spoofing. This process comprises verifying the host or server so that only the verified users can access resources deployed on the servers. It doesn’t demand any key or other means to initiate the process. However, the server should be competent to validate the login keys beforehand to keep the incidents of DNS spoofing, routing spoofing, and IP spoofing under control.
In the process and manner, it’s very much similar to RSA.
The argument used here is either yes or no. By default, no argument is set. The host-based verification of users can be done by an administrator by creating a private key for the local host or extracting the public key used for the localhost.
2. Basic authentication
One of the most straightforward API identity-confirmation schemes, this method is crafted using HTTP protocol and process as the client dispatches an HTTP request with a pre-built header for verification of authenticity and demanding credentials like account’s password and username. This basic check is done in a browser-powered environment.
Being supported by every possible browser and server makes basic identity-confirmation the most common one. The credential details are shared over the network in the form of cleartext and are encoded using base64. The credential details are shared over the network in the form of cleartext (or base64) by default, this is a bad practice since it gives man-in-the-middle attack vectors. The good practice is to encrypt the credentials using algorithms such as RSA, SHA-256 or even custom made ones.
It is functional over proxy servers and grants access to resources not hosted on IIS servers. As it fails to add encryption, not much security can be expected out of it. Also, it’s more prone to replay attacks.
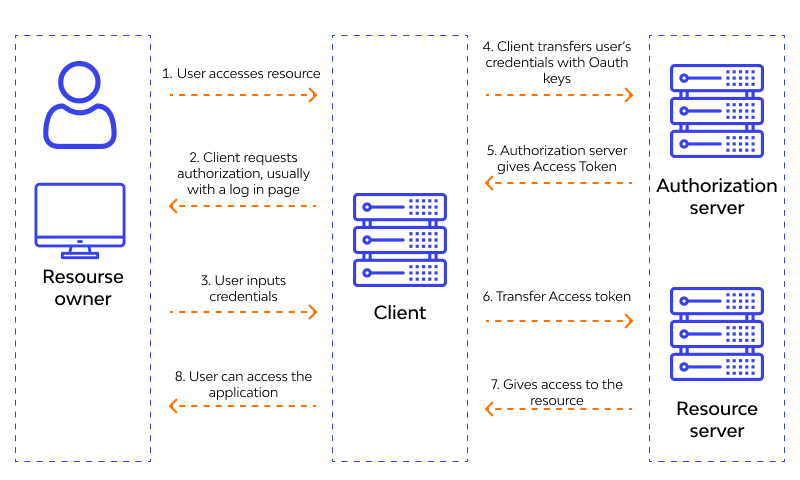
3. OAuth
OAuth is the open method of identity confirmation. It is a customary API authenticity-verification technique that covers users’ identity verification and defining authorization criteria. The protocol is used widely for allowing applications to authorize their users based on tokens, published from OAuth server (such as Google).
It requires asking for a token when someone tries logging into the system. The token serves here as the means of verifying and approving the user identity. The person/request-creator has to forward the request to accessing the resource to the authentication server. Based on the quality and result of identity-verification, the server can accept or reject the request.
OAuth is safer and more secure than other processes making it the first choice for many. The three key ingredients of OAuth are OAuth provider, Google and Facebook are the common ones, OAuth Client, refers to the information-owning website/page, and owner, denotes the user making an access request.
4. OAuth 2.0
A widely used protocol of API access management, OAuth 2.0 is an updated version of OAuth. Its functioning involves keeping the API client access limited by using HTTP services for the client application enabling. Some HTTP services needed for this sort of protocolare GitHub and Facebook. It takes the help of a code for identity-verification and doesn’t ask for user credentials.
The three factors involved in OAuth 2.0 are the user, who is possessing the data to which the API wants the view or edit permission, the application, and the API.
Using this method for identity confirmation, it’s easy to interpret user data using different resources. It can be deployed for the verification and approval of web-based, mobile-based, and desktop-based applications/devices.

5. SAML
SAML stands for Security Assertion Markup Language and is a standard API process for identity confirmation using single-sign-on technology. It denotes confirming the user as per the provided details. Once the process completes and the user is verified, access to assorted applications/resources is granted. Presently, its SAML 20 version is running. It’s very much similar to the ID. Only user identity assessment is done with its help.
What Does API Security Entail?
APIs, related to the app that you own, can only be controlled. This is why security API is focused on securing APIs that are exposed to a user, directly or indirectly. APIs, offered by other parties, that a user consumes are not a prime priority of Web API security as valuable insights related to such APIs can be gained by detailed analysis of outgoing API traffic.
One another key point to note here is that API security practice implementation involves multiple teams and systems. Network security principles like throttling, rate limiting, along with key data security concepts like identity-based security and analytics are a part of API security.
How To Pen Testing API?
Watch our webinar "API Threats Simulation With Open-Source Tools"
Read the guide - "How To Hack API"
Updated: We published online service - API Security testing platform - GoTestAPI
API Protocols
Based on the requirements, APIs can be used in various forms and styles. The chosen API style (REST, SOAP, GraphQL, gRPC, Websocket or Webhooks) decides how API security should be applied and implemented. Different API protocols, such as gRPC, GraphQL, and others, introduce their own unique security threats and attack vectors. For instance, GraphQL, due to its flexible querying capability, can be prone to resource exhaustion attacks if queries aren't properly validated and rate-limited. Each protocol, with its distinct architectural and operational nuances, requires specialized security considerations to address potential vulnerabilities and defend against tailored exploitation techniques.
API Protocol Comparison
How To Secure / Protection API And Cloud-Native Apps ?
Use Wallarm - a dependable and complete API security tool - designed to safeguard websites, microservices, and APIs from all sorts of dangers including OWASP API Top 10, bots, and application abuse easily.
The great part is Wallarm’s zero manual rule configuration and ultra-low false positives with Wallarm. Only reliable and real-time API security analysis and viable solutions will be offered. There is a free trial and demo offered for the convenience of the users. The tool is capable of protecting APIs of all sorts such as REST, SOAP.
Our seasoned API security team is skilled enough to secure APIs in any sort of environment. We have mastered the art and science of API security in AWS, GCP, Azure and IBM Cloud ecosystem, regardless of the type of deployment.
FAQ
References
Subscribe for the latest news